Published
- 5 min read
Windows Systems Infrastructure — Network & Server Design
🏢 Scenario
The project is based on a simulated client — Battlefield, a startup company headquartered in Toronto, Ontario.
The company operates a single main office and supports a total of 10 employees, including 2 system administrators responsible for IT infrastructure and maintenance.
As a 24/7 operation, Battlefield requires continuous internet connectivity, shared access to internal resources, and secure, reliable system availability for all departments. The network and system infrastructure must therefore be designed to ensure redundancy, scalability, and efficient management, while remaining cost-conscious to reflect the financial realities of a growing startup.
1. Design rationale and principles
Based on my preparation for the CCNP Encore exam and the knowledge I learned during the previous semesters, I designed the project following four principles: redundancy, security, optimization, and budget.
-
Redundancy, I considered from three perspectives:
a. Network. Layer 2 and 3 infrastructures should provide network reachability and path availability, and therefore need redundancy to maintain continuous connectivity. Use Virtual Router Redundancy Protocol (VRRP) or the Stack Over technique for L2/L3 redundancy.
b. System. Every functional system should have redundancy. Database Availability Group (DAG) is used for the Exchange server, and multi-master replication is used for the domain controller.
c. Data. Data redundancy should be multi-layer, including on-site (RAID) and periodic, encrypted off-site cloud backups.
-
Security.
a. Network: Three-zone-based security policy.
b. Wireless: Extensible Authentication Protocol (EAP).
c. System: Active Directory Domain Services (AD DS).
d. Remote Access: VPN.
-
Optimization.
a. Network: VLANs, Link Aggregation (LAG/EtherChannel), Access Control List (ACL), and Network Address Translation (NAT).
b. System-Level: Allocation of virtualization resources, storage performance optimization, and optimization of backup schedules.
c. Budget. Because of the start-up business, I could not consider it solely from a technical perspective; instead, I should find a balance between risk mitigation and practical feasibility.
2. Architecture overview
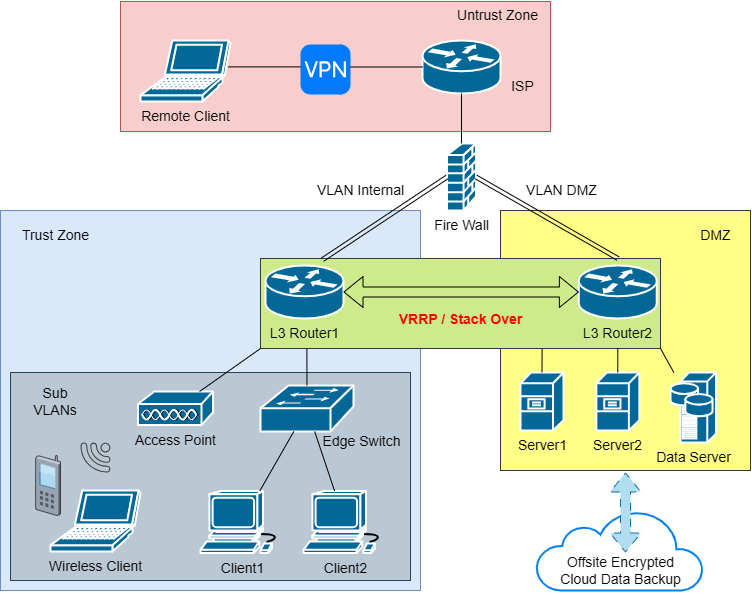
 ⬆ Figure 1 shows the network architecture.
⬆ Figure 1 shows the network architecture.
- There are three zones: the untrust zone (internet), the DMZ (servers), and the trust zone (internal).
- The two Layer 3 routers operate as a single logical device and connect to the firewall through two isolated interfaces (SPF+ ports). Each link is assigned to a parent VLAN that matches the security zone.
- In the trust (internal) zone, I designed the sub-VLANs for Layer 2 optimization by department, reducing the broadcast storm and improving the router performance.
- The sub-VLANs’ traffic is in the internal network; therefore, the firewall won’t get involved in the sub-VLANs’ traffic.
- All Layer 3 traffic between different parent VLANs must pass through the firewall.
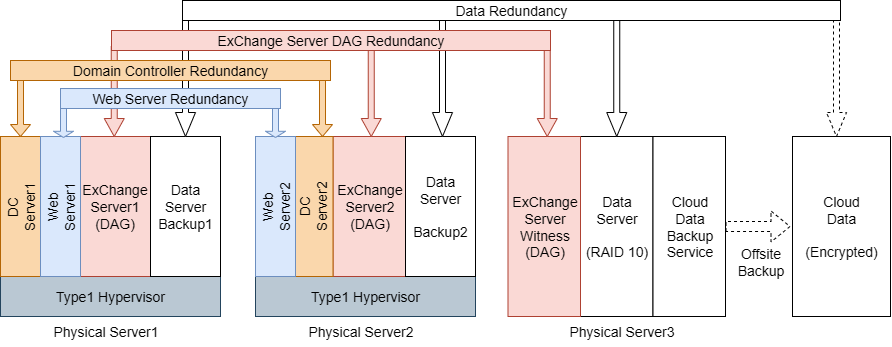 ⬆ Figure 2 shows the system virtualization and redundancy arrangements.
⬆ Figure 2 shows the system virtualization and redundancy arrangements.
- Considering the data load of a start-up environment, I designed two physical servers with Type-1 hypervisors to host four functional systems.
- Each virtualized host has four virtual machines: a Domain Controller (DC), a Web server, an Exchange server, and a Data server. The Exchange servers are in a Database Availability Group (DAG) for mailbox availability, and the other three systems are in a multi-master replication to provide redundancy to the systems.
- The third physical server operates as a dedicated Data server, uses RAID 10 storage to provide on-site data redundancy. This server also provides daily encrypted off-site backups to the cloud for disaster recovery.
- The third physical server hosts the Exchange Witness role, which participates in quorum arbitration to support DAG stability during node failures.
- The Data servers on the two virtualized hosts can retrieve synchronized data from the cloud in case of a local Data server failure, providing limited continuity for critical business data.
3. Implementation and configuration highlights
Network Layer:
- hierarchical VLAN design (parent-VLANs and sub-VLANs)
- Network Address Translation (NAT)
- Rapid Spanning Tree Protocol (RSTP)
- Open Shortest Path First (OSPF) routing
| Zone | VLAN ID | VLAN Name | Purpose / Department | IP Subnet | Gateway (L3) |
|---|---|---|---|---|---|
| Untrust | 10 | VLAN_Untrust | ISP / External Access | Public IP | N/A |
| DMZ | 20 | VLAN_DMZ | Servers Zone (S1, S2, S3) | 192.168.20.0 /24 | 192.168.20.1 |
| Trust | 30 | VLAN_Internal | Internal Corporate Network | 192.168.30.0 /24 | 192.168.30.1 |
| HR | 31 | VLAN_HR | (HR Devices) | 192.168.31.0 /24 | 192.168.31.1 |
| IT | 32 | VLAN_IT | (Admin, Servers) | 192.168.32.0 /24 | 192.168.32.1 |
| Sales | 33 | VLAN_Sales | (Workstations) | 192.168.33.0 /24 | 192.168.33.1 |
| Guest Wi-Fi | 34 | VLAN_Guest | Guest Wireless Network | 192.168.34.0 /24 | 192.168.34.1 |
⬆ Table 1 VLAN and Zone Allocation
System Layer:
- Active Directory Domain Services (AD DS) with Group Policy is implemented to have centralized access control and authentication.
- Network services are Exchange Server, DHCP, and DNS.
| OU / Department | Group Name | Role / Access Level | Assigned Users | Exchange Mail Access |
|---|---|---|---|---|
| Administration | Domain Admins | Full AD & Server Admin | Admin01, Admin02 | Global mailbox access, full control |
| Administration | IT Support | Limited system support | Tech01 | Internal email only |
| HR | HR_Staff | HR file & system access | HR01, HR02 | HR mailbox group |
| Sales | Sales_Staff | Sales apps & shared drive | Sales01-03 | Sales mailbox group |
| Finance | Finance_Staff | Accounting data access | Fin01, Fin02 | Finance mailbox group |
| Guests | Guest_WiFi | Internet only | Guest01 | No mailbox |
| Exchange System | Exchange | Mailbox & DAG | svc_EX01, svc_EX02 | Service accounts only |
⬆ Table 2 AD DS User and Access Design
Security Layer:
- Wireless security has EAP integrated with Active Directory for user authorization.
- Firewall policies are set based on zone-dependent communication policies.
- The guest wireless network has limited access to secure internal resources.
Maintenance and Automation: Day-to-day maintenance chores, such as backup administration, gathering of logs, and users’ accounts, are computer-automated with PowerShell scripts to minimize administrative labour and prevent configuration errors.
4. Reflection and summary
Strengths: For start-up companies, it is relatively balanced in terms of budget, reliability, and risk control. It has a clear security definition based on zone-level control, full multi-layer redundancy (data, system, and network), and a scalable form to support future growth. It shows high maintainability and flexibility for deploying in a small-to-medium enterprise.
Limitations: This existing single-firewall design still presents a possible single point of failure. Next generations can implement firewall clustering or a high-availability (HA) pair to remove this reliance.
Conclusion: In general, the design addresses the requirements of a start-up firm in terms of operating, security, and scale, but does so with realistic budgetary limitations. It shows a pragmatic engineering style that compromises performance, danger mitigation, and manageability.